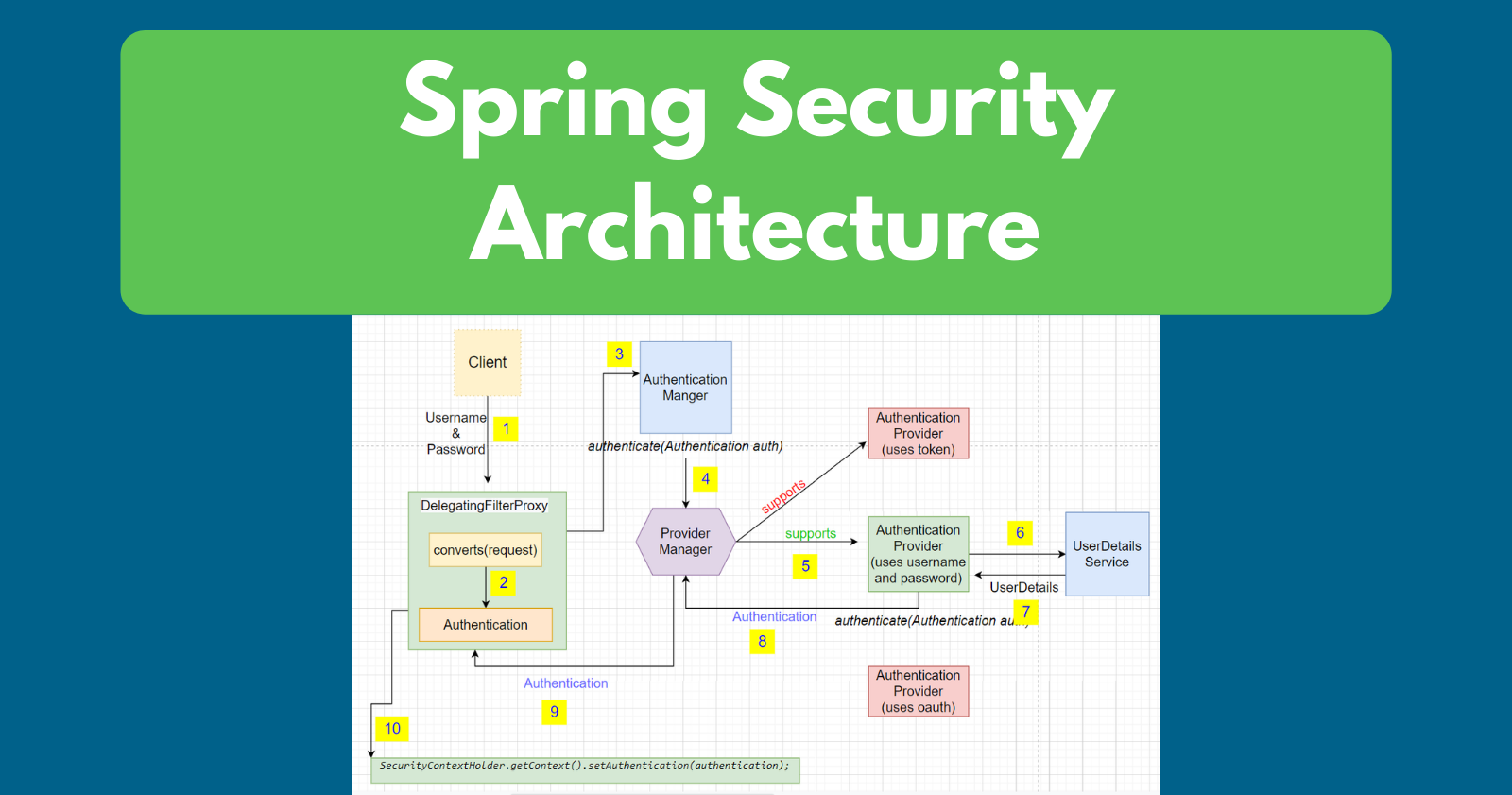
Product Name: Spring security top
Spring Security Interview Q A. 1. What is Spring Security by A cup of JAVA coffee with NeeSri Medium top, SpringSecurity Part 3 Spring Security Flow by Himaanshu Shukla Medium top, Architecture Spring Security top, How does Spring Security work internally by Haytam Benayed Medium top, What is Spring security Java Development Journal top, Demystifying Spring Security setup by Boudhayan Dev Medium top, 6.1. Spring Security Overview TERASOLUNA Server Framework for Java 5.x Development Guideline 5.0.1.RELEASE documentation top, Spring Security Architecture Explained top, The mechanism of Spring security top, Spring Security Medium top, Spring security authentication discount with database top, Spring Security Custom Pre Authentication Flow top, Spring Security Architecture and Internal Workflow top, Spring Boot Spring Security with JPA authentication and MySQL from scratch Java Brains top, Spring Security The Beginning. According to Wikipedia security is by Sabyasachi Mohanty Medium top, Spring Security Tutorials Java Code Geeks top, Understanding Spring Security. Spring Security is an essential by Wensen Ma Medium top, GitHub nonestack blog spring security basic authentication This guide walks you through the process of building a Spring boot application that uses Spring Security and Spring Data JPA. Applying the ne... top, 882KB 2001 null null null null null null null 1 2003 null cmBhcz0l6rvFjM top, Introduction to Spring Security Architecture by Rasheed Shaik Medium top, Secure development with Spring Boot Avatao top, Form Login Spring Security top, Security in microservices with Spring Boot and Kafka Lejdi Prifti top, Introduction to Spring Security by Pritam Kumar Dev Genius top, How To Implement Spring Boot Thymeleaf Security Login Example JavaTechOnline top, Dive into the Spring Security Architecture by Sohail Shah Medium top, Architecting Spring 5 Applications Spring Security and Its Architectural Design packtpub top, Spring security store authentication types top, The mechanism of Spring security top, Understanding Spring Security Authentication Flow by Ayush Singh Medium top, Authorization Architecture Spring Security top, Spring Security important concepts explained by Gurdip Singh Dev Tutorials top, Secure Reactive gRPC APIs with OAuth2 Using Spring Security 6 Stackademic top, Spring Security Java Configuration Annotation Example Dinesh on Java top, Spring Security Basic Authentication top.
Spring security top